Amid all the excitement surrounding the rapid transition to software-based, IP-connected media infrastructures, analysts are now raising a note of caution.
While the rush is to achieve operational and creative advances, there is a need to ensure adequate cyber security.
The recent highly publicised spread of the WannaCry virus should give everyone pause for thought.
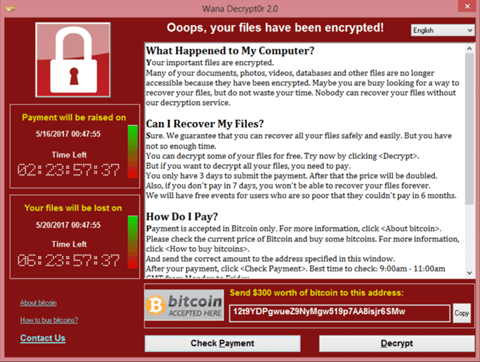
The move to the same open connectivity that is used by the rest of the IT world means that the media industry is also prey to the same risk of malware and hacking, as well as the potential for intellectual property theft.
In a recent article on IBC365 Denis Onuoha, Chief Information Security Officer at Arqiva, said of the move to IP: “This adoption has brought with it security vulnerabilities that simply didn’t exist previously.
“The only reason we are not seeing worms in broadcast yet is that broadcast has been living in this isolated environment.
“As soon as it gets more exposure it’s going to get hit and it will be hit ridiculously hard.”
Al Jazeera’s CTO Mohamed Abuagla went a step further, and claimed a direct correlation between the station’s news output and the nature of cyber attacks. “If we ran a story on government corruption in China, I would get Chinese attacks. If there was a story about the regime in Syria, we get Syrian attacks.”
The risk of intellectual property theft has been around for some time and has largely been well addressed, albeit in an ad hoc way. Content transport fabrics like Aframe, Aspera and Signiant have embedded protection to ensure content cannot be intercepted in transit.
But what about the growing numbers of software-based infrastructures? Typically these will have multiple points of contact, with maintenance and monitoring links between each piece of software and its vendor, as well as control and management at the system level.
IBC2017 Safety in Numbers: Collaborating Against Cyber-Attacks and Paper Session: Cyber and Content Security - Putting it into Practice
Phil Myers, IP product manager at SAM explained that it came down to good system design: “Protection is provided at two levels within the system. At the device level, a ‘hardened’ secure realtime operating system is implemented to provide isolation protection of all aspects of the device, including the file system and network stack.
“At the COTS network switch level, industry standard protocols can be implemented to secure the network,” according to Myers. He mentioned whitelists of valid addresses, which can control the flow of data in and out of a network.

Steve Reynolds, CTO of Imagine Communications, expanded on this idea. “The best practice for media companies is the segmentation of networks into zones of increasing trust. In general, critical control systems should be positioned inside isolated media networks, independent logically – and physically if possible – from broad corporate networks.
“If you secure operations and have trust elements built into the system, then you can stop an intruder doing anything with the content,” he added. “You can never guarantee that something bad will not happen, of course, but it does mean that hackers cannot go to air on your back.”
The message seems to be that there are technologies which, if rigorously applied, can provide the protection required.
And last year the EBU published its recommendations on best practices in cyber security, R143. It suggests a set of security safeguards to be applied when planning and designing media systems, software and services.
Yet best practice can be cumbersome and not cost effective.
Chris Fournelle is Director of Post Production at WGBH in Boston, and recently admitted that in their new workflows “we were breaking best practices. We knew it was not the way we should do it, but we have to get the show out.”
IBC2017 The C-Tech Forum: Cyber Security takes place at IBC on 15 September at the RAI. Click here to register your interest in attending the invitation-only event
























No comments yet